Hawaiian Telcom University: Q&A on Cybersecurity

Tags: Security, Events, Data Protection, Working Remotely, Cybersecurity
Cybersecurity is always a top concern with businesses no matter what size they are. During our recent Hawaiian Telcom University: How Does Your Cybersecurity Posture Stack Up event, our expert panelists answered numerous questions from the audience. Here's a list of the top questions.
Expert Panelists:
Matt Freeman (Director - Service Delivery, CBTS | Hawaiian Telcom)
Jordan Silva (Senior Manager – Service Delivery, CBTS | Hawaiian Telcom)
Dayne Yoshioka (Technical Support Group, ABC Stores)
Ryan Doi (Corporate Director of Information Systems, Prince Resorts Hawaii).
Q: What is the most critical step to take after a data breach?
A: The most critical step your business should take, even before a data breach, is to develop an incident response plan. It involves making sure the team knows who to contact and where to find information. Then, if the incident does occur, you and your staff can refer to this plan. You will then try to lock down the environment where the breach occurred as much as possible to determine the scope. Here is a helpful graphic to define the process:
NIST Incident Response Cycle
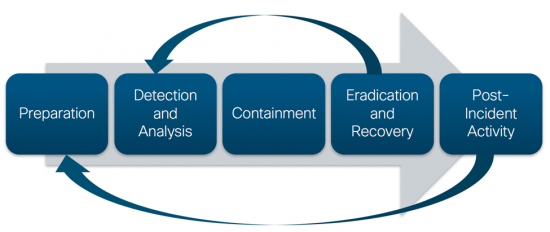
We encourage our customers/partners to conduct annual cybersecurity training for the entire staff. Also, it is important to remember that compliant organizations are required by law to follow the notification guidelines after an incident like this.
Q: How do you stop a tech-savvy person from VPNing in on a personal computer?
A: Originally VPNs were reliant solely on usernames and passwords for authentication, but modern VPN solutions can include hardware and software-based certificates and filtering methods. They can prevent non-approved devices from connecting to a VPN, or only allow limited access for unapproved devices.
Q: With us working from home, there is an increase in collaboration with cloud software. Are there risks involved with storing sensitive information on a cloud storage?
A: Of course there are risks involved, but they are not much more significant than when using onsite storage. It is important to remember to use trusted vendors for cloud services that go through their own compliance audits. Access control is always an issue. It is much easier to accidentally give more access than needed to someone in a cloud-based solution. Be aware of how access is given and how it can be shared. When it comes to precautions, they are very similar to the ones of the onsite storage. As long as you are working with a trusted partner and being mindful you should be safe.
Q: How do you keep users interested in learning about security without having a feeling of being overwhelmed or bored?
A: With a lot of annual compliance requirements you have to do some kind of annual training. It doesn’t need to be a long textbook-style training. For example, at Hawaiian Telcom and CBTS every October (Cybersecurity Awareness Month), we use a computer-based module to train our employees to get across the fundamentals of PCI, protecting customer data, etc. It’s a 15-20 minute module, it’s interactive, it has silly voices and animations, which makes it a little bit more fun. With ABC Stores we do regular tabletop exercises where you present different scenarios and determine a course of action. There are also lots of fun short videos on Youtube which should be helpful.
Q: We are strong with security operations but we need help with organization policies. Is HT a resource for that or do you have strong partners that can be shared?
A: CBTS offers a wide variety of security services, including security consulting services. We have helped multiple customers in the past with either improving or updating their corporate policies. In some cases, we’ve helped to build them from scratch. We can help with a comparison of your current cybersecurity posture and policy towards some of the compliance requirements. If you are not sure where to start we would recommend the CIS Top 20 as a good baselining. We can help with baselining against some of the major compliance frameworks and then help you to develop and improve your policy from there. We would encourage you to reach out to our experts and have a conversation about what you might be interested in.
Q: Do you guys have any recommendations on the applications that provide remote access without VPN or those that track file transfer?
A: It depends on many factors, such as your network and scale. If you have questions about specific applications or you need a recommendation, please reach out to our experts at htuniversity@hawaiiantel.net or give us a call at 777-6027. We’ll talk to you about your business and your network. We will definitely help you select applications based on your needs.
Q: What recommendations do you have for a small business or a new business with a limited budget that wants to start on the right foot with the security posture?
A: We would recommend starting with an assessment. Security is about identifying risks. Part of the risk is understanding where the most valuable assets on your network are, why they exist, and what they are worth. You also need to understand what are the legal requirements. Also, getting a trusted technology partner is highly recommended. Start with a consultation to identify your needs and priorities.
Q: I'm considering moving into a smaller office and have my staff work remotely. What kind of security platform do you use and what did you implement for Two Factor Authentication (2FA)? What are the pro/cons of switching to cloud vs VPN? Our business has slowed down so budget is a concern.
A: There are a lot of factors to consider when selecting a remote access technology. For example, a VPN allows remote workstations access that is very similar to being physically located on the network. For many pieces of software it is the only way to enable remote access. But the risk is that the device connecting also needs to be secure in order for your network to remain safe.
Remote Desktop to an on-premise workstation or a terminal server can be achieved without a VPN and allows for similar access, but with an extra layer between the user and the data. While it works well for many applications, some are not compatible or don’t perform well. Cloud-based applications like Office 365 are becoming more popular and when paired with cloud storage, it simplifies the connectivity methods. But they also introduce potential costs and risks; so an assessment of the organization's data and goals is needed to make an appropriate recommendation.
Regarding the question about Cloud vs VPN, there is cost-saving in each regard, but security always needs to be the top priority when making your choice. The right solution for your business will depend on your operation, your needs in terms of access and control, the sensitivity of your data, etc. Unfortunately, it’s not as easy as making a quick pro and con list, but we can definitely sit down with you and have a conversation about the right choice for you.
Do you have any questions about cybersecurity? You can reach out to our experts at 777-6027. Click Here to learn more about CBTS and Hawaiian Telcom Business Services.
*These questions and answers have been modified to fit the format of this post. To watch the original video from the event check out our Event Recap Post HERE.
Did you miss the event? Watch the full recorded session now!






