Whether you're splitting the brunch bill, buying concert tickets, or picking up a vintage find from online…
Filters:
Cybersecurity Articles
Whether you're browsing listings on Facebook Marketplace, scrolling through Instagram sellers, or checking…
Let’s be real: spotting a scam isn’t as easy as it used to be.
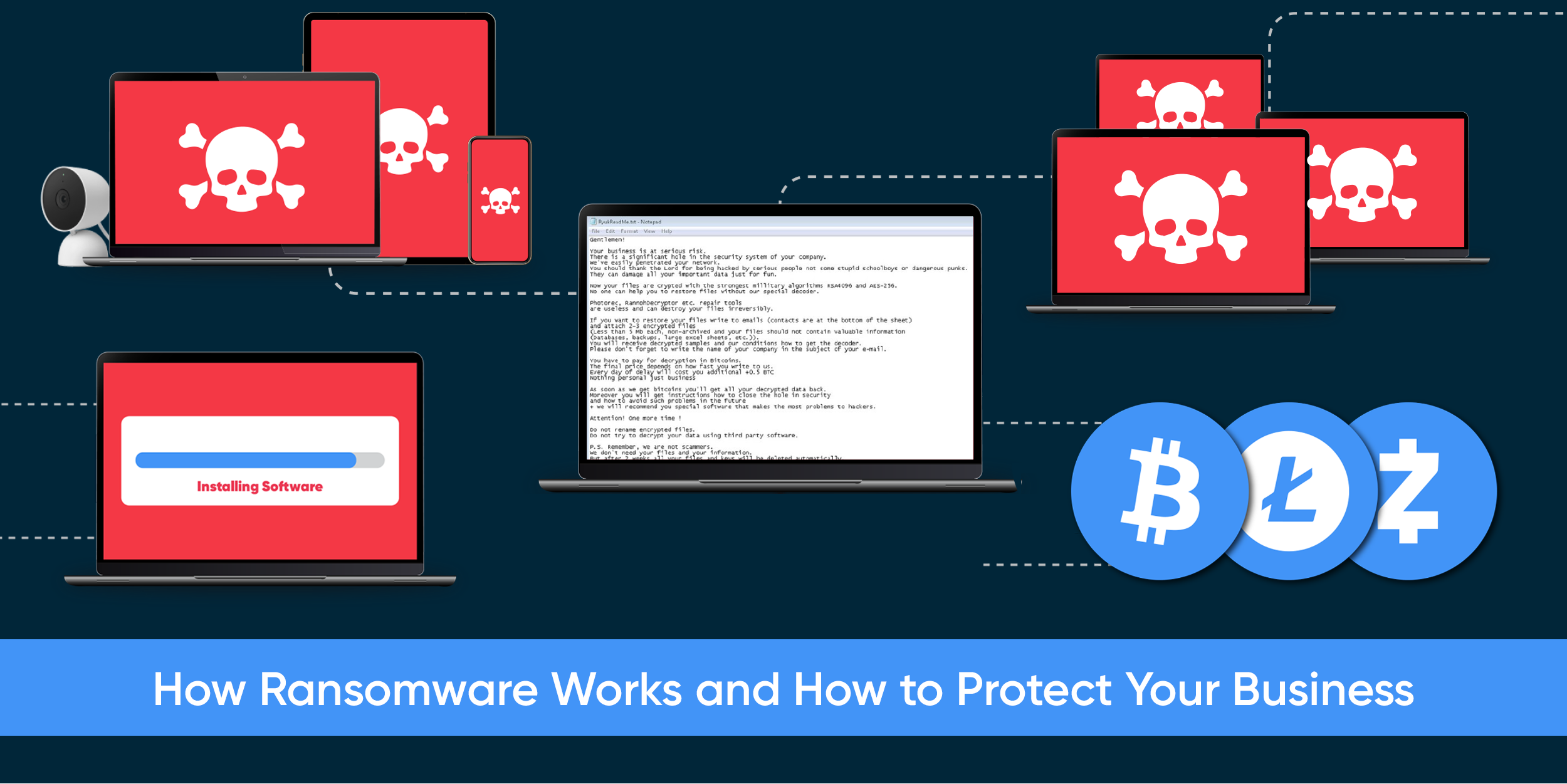
Ransomware is a type of cybercrime that has exploded in popularity and impact over the last decade. No…
The internet has made it possible for small businesses to thrive using digital tools for marketing, payments,…
|
Secure Network from Hawaiian Telcom empowers your business with unmatched protection, superior network… |
|
Hawaiian Telcomis pleased to announce the launch of Secure Network, an enterprise-grade network… |
71% of ransomware attacks impact small businesses. Aside from the devastating financial implications, a…
Recently, we have been noticing an uptick in a scam that targets people who are looking to make a better life…