Layered Security: What It Is & How It Protects Your Business

Tags: Security, Data Protection, Business Solutions, Managed IT, Cybersecurity
It's become increasingly common to hear about data breaches in our digitized world, and the cost of these breaches continues to climb to new heights. Not even Facebook has managed to come out unaffected by the unfortunate rise in cybercrime.
Many individuals and SMBs assume that cybercriminals focus their efforts primarily at larger companies like Facebook or enterprise-level corporations. The truth of the matter is that an attack could hit anyone.
Consider that in 2017, an agile ransomware attack sent waves worldwide, infecting over 230,000 machines within a single day.
This cyberattack resulted in considerable losses for businesses and even forced several UK hospitals to pause new patients' admission for a temporary period. Banks, telecoms, utilities, and many other industries experienced similar disruptions worldwide.
There are many security tactics and software solutions you can adopt to protect your business from sophisticated cyberattacks. A more comprehensive strategy is necessary if you're to be truly prepared.
One of the best ways to build a comprehensive IT security strategy is to take a layered security approach.
What is layered security? And why is it such an effective approach to IT security? We'll be exploring this and more in the sections below.
Breaking Down the Components of Layered Security
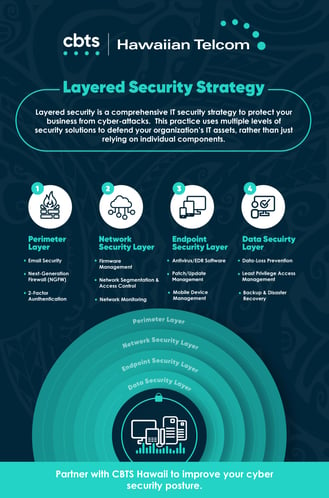
Layered security refers to the practice of using multiple levels of security to defend your organization’s IT security, rather than just relying on individual defense components, whether they be software security solutions or internal security protocols.
Cybersecurity professionals often break layered security into four main layers:
- Perimeter Layer
- Network Layer
- Endpoint Layer
- Data Security Layer
We’ll explore the components of each layer in greater detail below.
The Perimeter Security Layer
Server & Gateway security
At this layer, the goal is to limit who and what can come into your network. Preventing unnecessary exposure to the external internet via the use of firewalls, limiting the ability for malicious emails from getting to your staff, and making it more difficult to log on with a cracked or stolen passwords are common features of the perimeter layer.
Common perimeter security solutions include:
- Email Security
- Next-generation firewalls (NGFW)
- 2-Factor Authentication
The Network Security Layer
Network Availability and Monitoring
This layer deals with the security of your local physical and wireless networks. It is what connects your endpoints to your servers, to each other, and to the internet. The IT security practices you implement here serve to keep your network secure and consistently available.
Side Note: When businesses experience disruption due to a cyberattack or other event, the highest cost is usually associated with downtime and disruption of critical business services.
Modern network monitoring solutions should provide you with a detailed inventory of all the devices on your network. Your network manager should be able to quickly identify any devices having issues and prevent disruptions before they occur. Knowing how your business's network is doing at any given moment will help you identify and isolate any potential threats before becoming real problems. In addition to the visibility into what is on the network, a program to manage the install of firmware upgrades to things like routers, switches, and access points is critical to the security and stability of your network.
Effective network segmentation and regular audits of access control lists (the "rules" that determine who/what can access segments of your network) will help limit the effectiveness of an attack if it does get past your perimeter security.
Proper logging and monitoring also allow you to speed up your response time to disruptions, bolstering your business's ability to resolve network issues and maintain high availability of services.
Virtual private networks (VPNs) can be used to extend the security of your local network to those working remotely. With the rise of remote work, it's never been more important to keep your business's information secure when your employees access your network from home or in public spaces. A VPN uses encryption to prevent malicious third parties from intercepting traffic and helps keep data on your secure network instead of on remote workstations.
Common Network Security Solutions Include:
- Firmware Management
- Network Segmentation and Access Control
- Network Monitoring
The Endpoint Security Layer
Endpoint security refers to securing the devices employees use day-to-day (e.g., laptops, desktops, cell phones, tablets). This helps prevent these devices from being compromised by cybercriminals and being used to access other areas of your network, like the servers that store your data.
A good antivirus or EDR (Endpoint Detection and Response) solution is an essential component of this layer. It detects and often stops malware from getting a foothold on your workstation and from spreading to others.
Software not only needs to be installed but also kept updated and have a mechanism of notifying your IT team when it detects a problem.
Combined with an effective and managed software update/patching program and a mobile device management solution to secure things like tablets or cell phones, and you are well on your way to securing the part of your network your staff interacts with the most.
Mobile devices have become an integral part of our society. For most companies, they might as well be considered pocket-sized computers, and like their larger counterparts, they can pose a risk to your IT security.
Companies have been using bring your own device (BYOD) policies for a while now, but such policies might not be compliant with data privacy laws or pose potential security risks.
An effective mobile device management tool can help you ensure that individuals devices are using security best practices like local encryption, pin/passcode access, and ensure that updates are being applied to the devices on a regular basis.
Having well-thought-out policy management for mobile devices and software solutions also helps limit the risks associated with mobile devices without sacrificing the convenience they bring to your company.
Common Endpoint Security Layer Solutions Include:
- Antivirus / EDR Software
- Patch/Update Management
- Mobile Device Management
The Data Security Layer
The data security layer addresses the actual information a company stores. While the other layers focus heavily on devices on the network, this layer focuses on the "crown jewels" - your information.
The use of Data-Loss Prevention (DLP) technology helps ensure that sensitive or proprietary data doesn't leave your secure environment. Most Data loss events are accidental, not malicious, but DLP technology helps prevent both.
A concerted effort to implement "least privilege" methodologies, where individuals are only granted access to data needed for their specific role, helps limit the effects of attacks if they are able to obtain a users credentials and helps the accidental or intentional damage or loss of information.
And finally, a regularly tested Backup and Disaster Recovery (BDR) solution should be in place to ensure that in the event the other layers fail you are able to safely and securely restore your data. When selecting a BDR solution, be sure to look at how long that restore process could take, and ensure that aligns with your business needs. Often, cheaper solutions look attractive, but the time they take to restore large volumes of data leaves the companies using them offline much longer than anticipated, which could be a costly mistake. Not all backups function in the same way, some only backup specific files and can't be used to fully restore in a disaster scenario without first manually reinstalling all software required, then restoring the data. Others take snapshots of servers and can fully restore them very quickly as needed. Understanding what you have, and which you need, is key for a successful recovery.
Common Data Security Layer Solutions Include:
- Data-Loss Prevention Software
- Least Privilege Access Management
- Backup and Disaster Recovery
Compliance Frameworks and Security Baselines
The challenges of protecting a network can seem overwhelming at times. One approach to getting started is adopting a known security compliance framework. For some businesses, there are specific requirements they are required to follow; HIPAA for medical providers and PCI-DSS for those who accept credit card payments are two of the more well-known.
For organizations not required to follow a standard compliance framework, there are still others available to help, like NIST 800-53 or the CIS Top 20 Controls
Reporting, Updates & IT audits
Once you begin implementing, upkeep becomes critical. Even when your company has solid cybersecurity in place, you'll want to audit your IT security infrastructure at least annually to take technological changes and updates into account. Cybersecurity audits are vital to discovering issues that get lost in day-to-day business.
Managing and installing updates to your software is especially important because updates often come with security patches that fix issues that might otherwise allow cybercriminals to exploit vulnerabilities in the software.
If you have a comprehensive IT security solution that monitors your security infrastructure, it should allow you to gather detailed IT reporting data on how many threats get detected/locked down, where your systems may be vulnerable, and many other valuable data points. Regular reporting on systems helps ensure that what you believe is happening is actually happening.
If you don't have a software solution or IT specialist that does this level of reporting for you, you may want to consider hiring an IT security auditor to handle this task for you.
Adopting Layered Security for Your Business
Every seasoned IT security professional understands the value of using multiple cybersecurity solutions to provide the greatest level of security possible for your company. Adopting a layered security approach can keep your security solutions organized and agile enough to respond to ever-evolving world of cyber threats.
CBTS Hawaiian Telcom provides a wide range of IT security products, resources, and other tools to help your company achieve greater security levels as you continue to grow.