How Ransomware Works and How to Protect Your Business
Ransomware is a type of cybercrime that has exploded in popularity and impact over the last decade. No business owner wants their system infected with malware of any kind, but a ransomware attack can leave an owner feeling particularly powerless—and facing costs that could devastate a small business. Here’s what you need to know about ransomware attacks.
How Ransomware Works
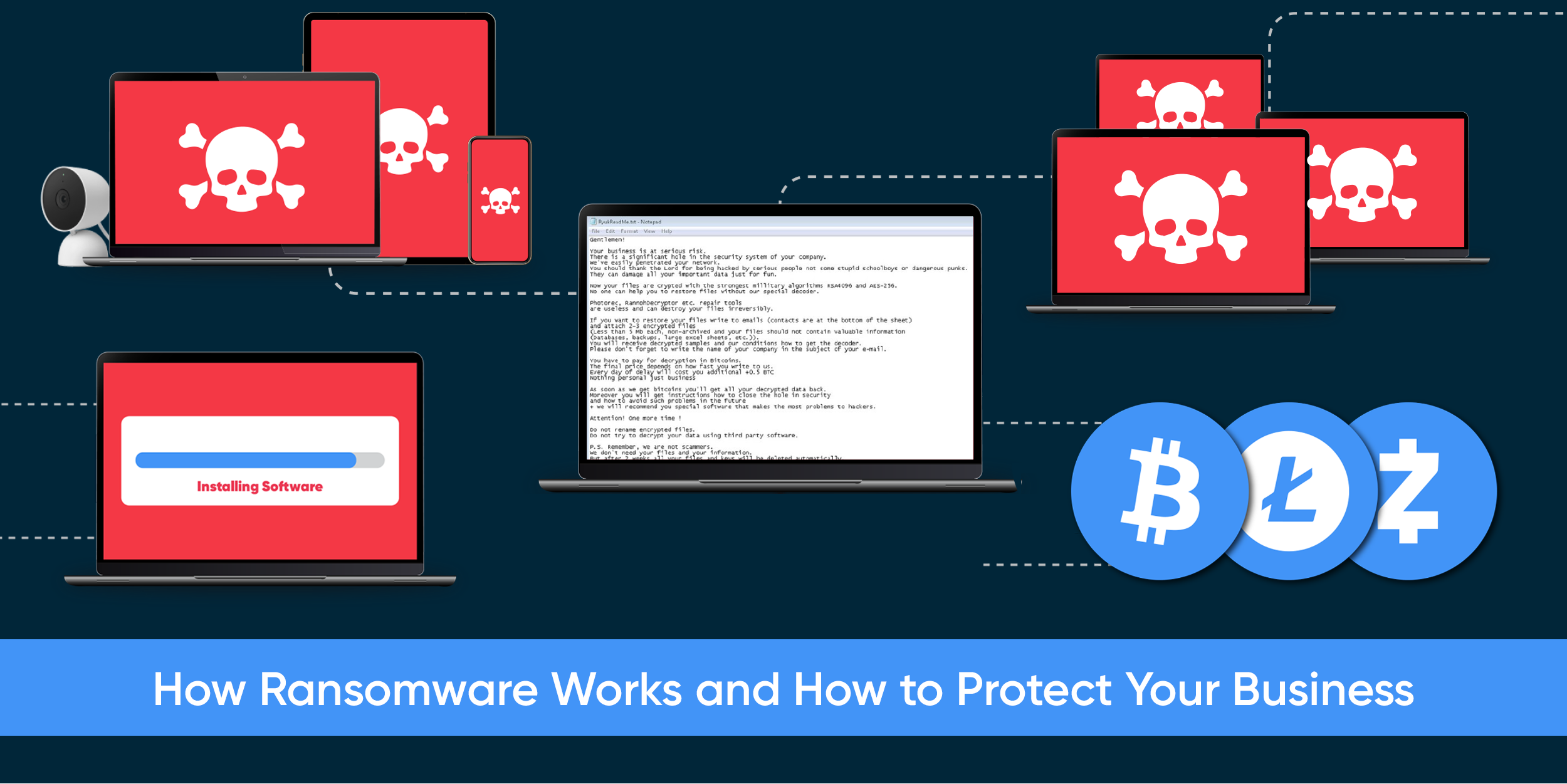
- Hackers exploit vulnerabilities, such as outdated firmware, in the devices connected to your business network. These devices could be printers, smart speakers, point-of-sale systems, etc.
- Ransomware takes advantage of a vulnerability in the operating system or software to run the infecting code.
- The ransomware code encrypts the data on the system, locking it so that only the attacker can access it.
- The attacker will demand a payment in exchange for restoring your access to your business and keeping sensitive data private. Usually, this payment is in Bitcoin or some other cryptocurrency, which keeps the attacker anonymous.
- Often, ransomware will spread to other devices on the network, multiplying the vectors for attack.
Click here to download the How Ransomware Works infographic.
Ransomware Creates a Vicious Cycle
For small businesses, the payment to a ransomware attacker can be ruinous — hundreds of thousands, or even millions, of dollars. But ransomware can damage an organization’s reputation as well as its bottom line, which incentivizes companies to pay the ransom to avoid being exposed. Successful attacks create a vicious cycle of more hackers mounting escalated attacks for ever-higher payouts.
Protect Your Business Against Ransomware
Adopt a proactive approach to cybersecurity, to protect your business and your customers:
-
Regularly Back Up Data: Ensure all critical business data is regularly backed up and stored in an offline location. This practice allows businesses to restore their data without paying a ransom.
-
Implement Multi-Factor Authentication (MFA): Use MFA for all critical systems and accounts to add an extra layer of security beyond just passwords, making unauthorized access more difficult.
-
Conduct Employee Training: Educate employees about phishing scams, suspicious email attachments, and the importance of not clicking on unverified links. Awareness is a critical defense against ransomware.
-
Keep Software Up to Date: Regularly update operating systems, software, and applications to patch security vulnerabilities that ransomware can exploit.
-
Deploy Anti-Malware and Antivirus Software: Use reputable anti-malware and antivirus software to detect and block ransomware before it can encrypt files.
-
Create an Incident Response Plan: Develop and regularly test an incident response plan outlining the steps to take if a ransomware attack occurs. This plan should include isolating affected systems and notifying relevant stakeholders.
-
Segment Networks: Segment the network by separating employee and guest WiFi. Restrict access based on user roles and responsibilities to minimize potential damage.
Stay Cybersafe with Secure Network
60% of small businesses that suffer a cyberattack close down within six months, but you can protect your company from ransomware and a potential closure with Secure Network from Hawaiian Telcom. Secure Network is a state-of-the-art cybersecurity solution that empowers your business with unmatched protection and a premium WiFi experience.
Contact us today to learn more about how Hawaiian Telcom can elevate your cybersecurity and network performance. Call 808-777-6027 or visit our website to learn more.